Until @tjluoma posts something more definitive here’s a brief look at setting up SSH for Shortcuts.
First of all, you will need to ensure you have a terminal app and are able to login to your ‘box’. This could be utilising a username and password credential-based login or an existing SSH login. There are steps to take to ensure you can only use SSH with an account that are also worth looking into.
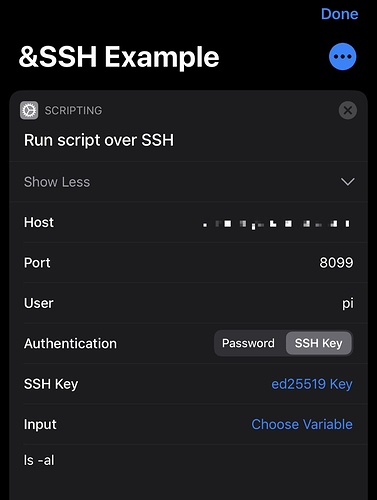
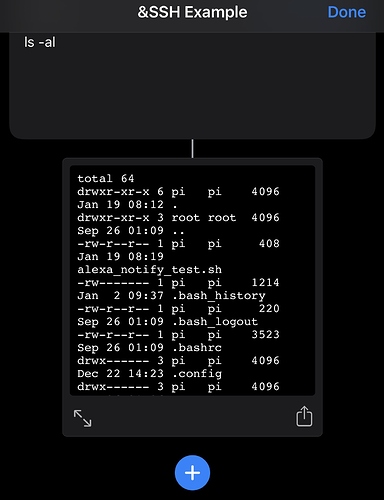
Let’s begin with a simple SSH action in Shortcuts to list files using ls - al
Here I’m connecting to one of my Raspberry Pi machines, and it is accessible over a non-standard port. Note that the action has been set to use an SSH key.
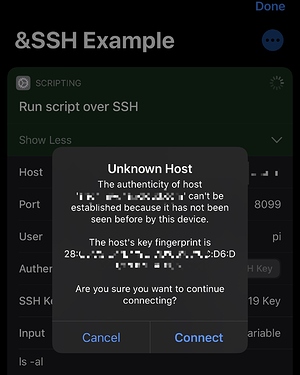
If I run this action, I get some fingerprint details to confirm to ensure this really is my box. Happy that it is, I select Connect.
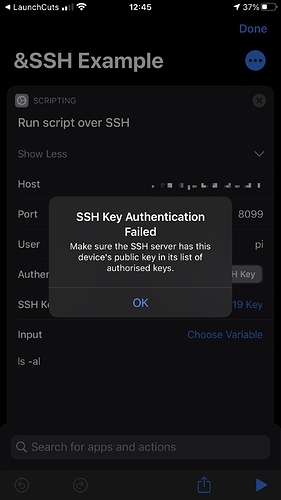
But this connection will fail as my box doesn’t know to trust my key. I need to add my public key to the list of authorised keys on the box.
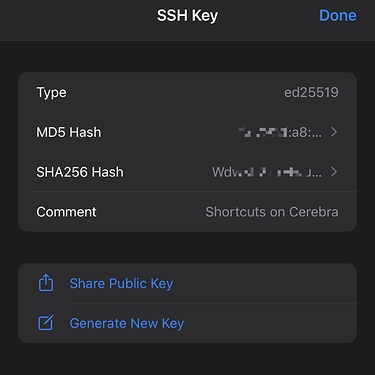
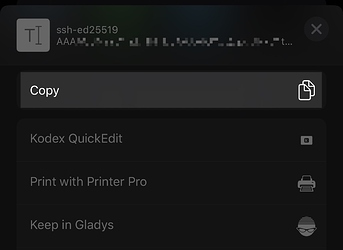
Tapping on the blue text of the SSH Key in the shortcut action takes me to a window where you can share the public key.
The key has a note about this being for Shortcuts for my iPhone, which is useful. Select the option to share, and copy the key.
You now need to login to your box using a terminal app. There are many out there. Free and commercial. Pick one you trust, or even use a terminal connection from a Mac or PC. Just ensure you have tthe copied public key on that machine.
Once logged in as the user you want to use (“pi” in my case), type in the following command.
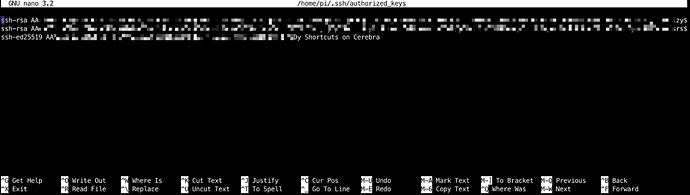
sudo nano ~/.ssh/authorized_keys
You might not need the sudo, but I’ve had a mix of success on different machines, so I just use it by default. Non-US folks, note also that this uses American English spelling.
This command will open the authorised keys listing file in an editor called nano.
Paste the public key entry on a new line at the end of the file, then press CTRL+S to save, and CTRL+X to exit. Your key is now in the list of authorised keys. You can exit.
Now when I run my SSH action, it completes with no further interaction and I can see the file listing coming through as output.
There’s more to dig into on SSH. Things like port exposure/port forwarding can be considered, disabling username and password login or at least limiting consecutive login attempts, etc., but hopefully the above gives a few pointers to get started.